- 1. Last year in December (sounds like it was a long time ago) I had the pleasure of publishing my first ever Medium post. Its purpose was to highlight the importance of proper vendor selection management and present the consequences that may come into play when you underestimate the risk of doing it wrong. You are welcome to check it out here.
- 2. Step 1: Create and consolidate the list of vendors
- 3. Step 2: Create a list of services that you consider relevant to your organization
- 4. Step 3: Find relations between vendors and services
- 5. Step 4: Verify the need for creating Vendor Risk Profiles
- 6. Step 5: Create a Vendor Risk Profile
- 7. Step 6: Check the vendor compliance and assess risks using a self-assessment
- 8. Step 7: Gaps and findings management
- 9. Step 8: Risks Mitigation to identified findings (Probability/Impact matrix)
Last year in December (sounds like it was a long time ago) I had the pleasure of publishing my first ever Medium post. Its purpose was to highlight the importance of proper vendor selection management and present the consequences that may come into play when you underestimate the risk of doing it wrong. You are welcome to check it out here.
This time, I’ve focused on a little bit more practical approach and to continue the thread I’d like to share with you some tips on how to build efficient and long-term risk management processes.
Yes, vendor selection is a process. It can be managed, introduced step by step and run for as long as you wish to avoid the risk of making bad subcontractor choices. Establishing the vendor management program in your company requires 8 steps. I had an opportunity to present this approach last year on ISACA (known as Information Systems Audit and Control Association) conference organized to celebrate the organization’s 50th anniversary.
Step 1: Create and consolidate the list of vendors
Yes, it’s that simple. List them all, make a table with their names, addresses, names of your contacts over there and their emails. Sometimes this activity would be easier to deliver as part of a Vendor Consolidation Project. It’s also helpful to have this information standardized.
Step 2: Create a list of services that you consider relevant to your organization
What services does your organization need? Think of all of them and make a list. This list should include every service that the organization receives from third parties. Each service should be assigned with a significance rating which indicates the importance of the service to the enterprise business. Using a finite numerical scale or a set of the quality descriptors for this rating is recommended.
An example list of services:
- Accounting services
- Legal services
- IT systems services
- Human resources support services
- Office cleaning services
- Application hosting services
- Data processing services
- Big data analytics
- Physical security and building access control
Now, you can probably guess what the next step is.
Step 3: Find relations between vendors and services
Yes. Combine the tables! Just assign suppliers from the vendor list to the services your company needs and find the links. The links allow an organization to identify the providers that require special attention (e.g. those that process enterprise data, including personal data, or host enterprise IT systems).
A provider may offer multiple services. Sometimes, the linking process reveals that some vendors do not have assigned services, or some services do not have assigned vendors. If this is the case, the organization should answer the following questions and resolve any issues:
- Is the vendor list complete?
- Is the services list complete?
- Why does the enterprise need a vendor that is not delivering a value (no services assigned)?
Step 4: Verify the need for creating Vendor Risk Profiles
Creating a risk profile for each vendor will let you understand how essential their services and/or products are for your organization. They also let you have a better look at your relationships and define what type access (physical, IT, data) to give to the vendor.
Filtering criteria used in the profiles should be harmonized in the organization. There must be no exceptions to that.
Step 5: Create a Vendor Risk Profile
The enterprise assesses each third-party regarding two aspects:
- Aspect 1 — Risk linked to the organization maturity of the third party as a result of it running its day-to-day business activity.
- Aspect 2 — Risk linked to the services rendered to the enterprise by the third party.
It is recommended to include the risk criteria below to build the profile. You have to leverage knowledge available in your organization (it’s a MUST). You can enrich the data with additional information sources (like D&B, Bisnode etc.)
Services risks:
- Compliance and regulatory risks related to the service
- Customer and financial impact
- Criticality level of the service delivered by the vendor for our company
- Financial transactions processed
- Personal and sensitive data involved?
- Maturity of the service?
Entity risks:
- Maturity of the service?
- Location of the vendor
- Known security incidents
- Size of the company
- Financial standings
- Performance history
It is important to understand that a created risk profile for enterprise providers may change over Time. This is not a one-time activity. This is a continuous process that should be repeated annually (at least).
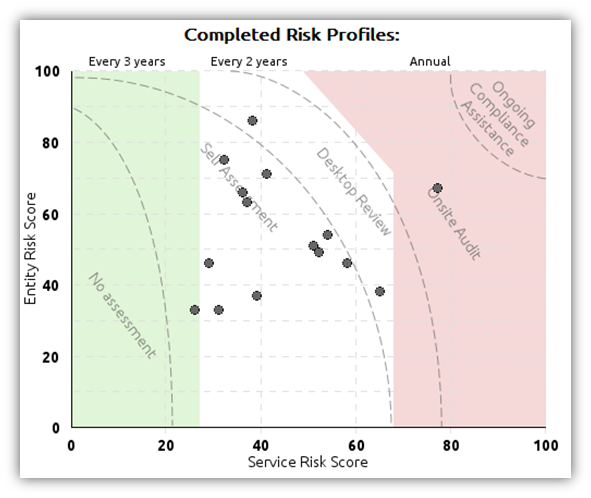
Step 6: Check the vendor compliance and assess risks using a self-assessment
It is possible for your vendors to carry out the self-due diligence activity, especially, when you provide them with tools to do that. All your vendors should be required to complete self-assessment and enabling them to fill a risk assessment questionnaire template is a great idea. These online forms can be prepared well in advance, either as spreadsheets or a dedicated online polling system.
Step 7: Gaps and findings management
After the necessary information is collected via assessment, you can carry out the evaluation process and determine the order of corrective measures, as well as establish a list of activities and assign them to people responsible. The corrective measures may concern both your organization and individual vendors.
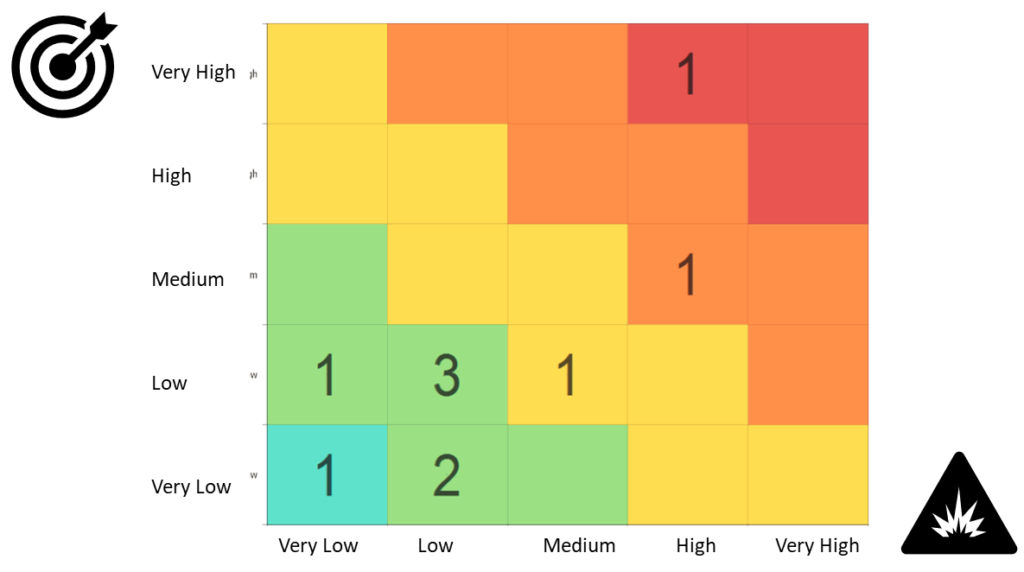
Step 8: Risks Mitigation to identified findings (Probability/Impact matrix)
Probability and Impact Matrix combines the probability of risk occurrence with impact scores and enables their prioritization. Build it to determine which risks should be considered and answered with proper response.
Vendor management is a process. Start small, make first steps and then grow the process to become a program. It’s not about winning the race, It’s about taking proper part in it.
You are welcome to contact me if you have any questions or would like to discuss the details on a more complex level.
Would you like more information about this topic?
Complete the form below.
